Wednesday, 29 July 2015
Guys! Suppose you are playing any game or using any other application while internet connectivity then a lot of ads in footer or header area are shown. This is really annoying and wastes the bandwidth up to some extent.
So, the next question is who to remove those ads. There are basically two methods. The first one is either you buy the app which you never gonna do anyway or you block the ads by blocking proxy which let the apps to connect to the ads network.
Here is demonstrated NoRoot Firewall app for the android platform. There is another app named Droidwall. What makes the difference? NoRoot as the name signifies also works with full functionality on non-routed phones where as Droidwall requires root privileges.
Home Screen is shown firstly when you start the app. This screen has START/STOP control.
Now there are various others tabs which include PENDING ACCESS, APPS, GLOBAL FILTERS, and ACCESS LOGS. Each tab has its own functionality and is/are described below shortly.
PENDING ACCESS
It shows all the apps which ping the network. It will ask you to ALLOW or DENY access. If it is a system app then allow the access else tap deny. But wait, if you deny the whole services of that app will be blocked. You only want to block the ads, not the complete internet access. Now what to do? Tap on that particular app and you will see all the proxies which want internet access. If a particular proxy is pinging the ads then block it by double cross sign else allow it.
APPS
It shows the list of all the apps which are installed on your devices either it is a system app or post installed ones. If you tap on any particular app you will see Add Custom Filter. This option allows you to allow/deny access to the internet for proxies.
GLOBAL FILTERS
This is most amazing. Here if you add a proxy to Pre-filter then that proxy will be blocked for all apps instead you need to add custom filters for all apps for that proxy.
ACCESS LOGS
In this tab, you can monitor all the proxies which one is having access allowed and denied and pending access as well.
Note:
1. The more you spend time with something the more you will know about that thing..
2. Your Wi-Fi hotspot might show a limited connection when this firewall is enabled.
Social Engineering
01:44 BackBenchers World
This
is a technique where we use brain rather than tools. We obtain critical
information from victim’s ignorance or
lack of knowledge.
How
a password should be??
A password must
be a combination of small letters, block
letters, numbers and symbols with a minimum of 12 characters. Most of the
time one set his passwords related to his personal life like flowers,
actor/actress names, mobile numbers, date of birth, pet name, mother’s or
father’s name, lover’s name or common words like 123456 etc.
If your
passwords are in this category then it’s very easy to compromise your account within a short time interval. So never set password related to your
personal life and make sure to categorise your password into five types.
- Confidential Password
- Financial Password
- Useless Password
- Average Password
- Normal Password
Confidential Password:
Is it required
for everyone to know what you are chatting at midnights with your personals???
If your answer is “NO” then set
confidential passwords to those specific websites like Facebook, Gmail, Yahoo
etc. And don’t use those confidential
passwords anywhere else.
Financial Password:
Set a very strong password for websites where
you do financial transactions and never use that password anywhere else.
Useless, Normal, Average Password:
Based upon the
priority of the site set useless, normal, average passwords.
Wrong is always right:
Never set a
correct answer for your recovery questions. Always set a wrong answer for it and don’t forget what you set.
Sunday, 26 July 2015
How To Hide Files Behind Image
19:16 BackBenchers World
This
technique is called as Stenography. It involves hiding data behind
images so that only the intended recipients can read the message being
sent. I will show you how to hide files inside a picture file. They are
almost undetectable, and can be made very hard to get. You can not only
hide files in pictures, but music files, videos, and just about anything
else.
There are so many S-tools available to hide data behind images. But here you don't need any tool for this. You will need these things:
1) A picture to hide stuff in
2) Files to be hidden
3) A file compression software (I’m using Winrar)
4) Command Prompt
So here we go.
Step 1: Add the data files to a single .rar file and place a image file in the directory containing the rar file.
Step 2: Open Black Box (Command Prompt). [Press windows key + r. Type cmd and press enter. It will open black box.]
Step 3: Select the Disk Drive by writing drive_name: and peress enter. E.g. desktop: or c: or d:.
Step 2: Open Black Box (Command Prompt). [Press windows key + r. Type cmd and press enter. It will open black box.]
Step 3: Select the Disk Drive by writing drive_name: and peress enter. E.g. desktop: or c: or d:.
Step 4: Now type the command copy /b <Image.jpeg> + <File.rar> <New_name.jpeg>. And press enter and its done.
Note: Don't include < > while running the command. These sign(s) are only enclosing a file_name with it's extension.
Note: Don't include < > while running the command. These sign(s) are only enclosing a file_name with it's extension.
Now you would like to know how to excess that hidden file.
What you have to do is only to open that image file with winrar. It will open the rar file hidden behind image file.
What you have to do is only to open that image file with winrar. It will open the rar file hidden behind image file.
For that:
1. Right click on image file containing the hidden rar file.
2. Goto Open with and chose Winrar. And the hidden rar file is opened.
Note:
Don't make winrar a default program to open that file. Else it will
open the hidden rar file whenever you open it by double clicking on it.
How To Unhide Hidden File-Folder On USB
03:10 BackBenchers World
When
your folders go missing on your computer or your storage device, or
simply created shortcuts in each of them, then they are infected with a
virus, actually not a virus. So let's get to know how to get rid of it..
Step 1:
Open the Command Prompt. You can find it under "Accessories" or just search for "CMD" on search bar of your Windows computer.
Step 2:
Step 2:
Find
out in what drive of your computer the virus/shortcut are located. Go
to My Computer (for Windows 7 or below) or This PC; you'll notice the C,
D, E, etc drives.
Step 3:
Step 3:
Go to CMD and type in the commands.
For example, the virus is located in "F" drive, then just type <attrib -h -r -s /s /d f:\*.*, the F beside the D is your drive; simply change it to where drive the virus is located.
- -h: to unhide all files on drive W
- -r: create the files in drive W is free of read-only attribute.
- -s: making all files on drive W to be not part of the system again, so easy in the clear
- f: w drive
- *. *: All files ending in
Step 4:
Press
Enter. The bigger the files, the longer the processing takes. Wait
until you see "C\:Users.." again. It means that drive will unhide all
the folders in your drive.
Step 5:
Step 5:
Check
your drive again. The folders are now retrieved together with the
shortcut viruses. Remove unnecessary files, the shortcut files that are
not supposed to be there. You might find autorun.inf or desktop.ini;
simply delete them.
How to create a recovery media for Ubuntu 12.04 LTS installed on DU laptops
02:03 BackBenchers World
Delhi
University has given Laptops to the 1st year students so that they may use it for their
studies. These are having a pre-installed Ubuntu
12.04 LTS operating system on it. This OS is far more different from Windows OS although both the OSes have a GUI (Graphical User Interface). If you want to install Windows OS, you can also do it. The Whole procedure is discussed in the link given right here.
Related: How to Install OS using pendrive
With this Laptop no DVD/CD reader-writer is available. So here is discussed how to create a backup image of present
Ubuntu OS to recover the Laptop to factory state by using pendrive. So it starts with creating a backup image (.ios file).
This is
how your home screen look like.
Step 1:
Goto
Dash Home and type Startup Disk Creator and open the
application.
A
dialog box will appear. Here click on OK.
Step 3:
It will ask you to choose a location to
save the iso file. You can select any location. Let’s select Desktop and click choose.
Step 4:
It’s almost done. Wait for a while.
Step 5:
The backup file is created as HP_Recovery on the desktop.
Step 6:
Now create a Bootable USB Stick with
this image (iso file). Now you can easily reinstall Ubuntu 12.04 LTS using this USB Sick if you installed any other OS on this laptop.
Related: How To Make Bootable USB Stick
Saturday, 25 July 2015
How To Install OS From Pendrive
23:14 BackBenchers World
In order to install any operating system through pendrive you need to make it(pendrive) bootable by writing the required files to install OS. You can use either .iso or .nrg file format images. Here in this post .iso file has been used for demonstration. There are various software tools which can be used to burn the image file to the pendrive. But using any random tool can be hazardous as they might left your USB stick with permanent memory loss i.e. you
might not be able to use your pendrive for data storage further.
Here is demonstrated Power ISO. Don't worry this is a trusted software and won’t cause any memory loss to your pendrive. You can
download it from Power ISO official site or you may simply click the links
given below.
Here step-by-step procedure is explained with screenshoots. Even if you
find any difficulty then feel free to contact us or you can just drop a
comment.
So here we go.
Step 1:
Plug-in your Pendrive.
Plug-in your Pendrive.
Step 2:
Open PowerISO in administrator mode. For this right-click on PowerISO icon and select Run as adminstrator.
Open PowerISO in administrator mode. For this right-click on PowerISO icon and select Run as adminstrator.
Step 3:
Goto Tools option in the menu bar and select Create Bootable USB Drive.
Goto Tools option in the menu bar and select Create Bootable USB Drive.
Step 4:
A dialog box will be as in image below.
A dialog box will be as in image below.
Step 5:
Here select Image Source File, Destination Derive and Write Method. Finally click Start. It will take some time to get yours' usb stick ready. So wait until the writing/burning process get finished. Then click OK.
Here select Image Source File, Destination Derive and Write Method. Finally click Start. It will take some time to get yours' usb stick ready. So wait until the writing/burning process get finished. Then click OK.
Step 6:
Now you need to change the boot priority in the BIOS. You need to set the 1st booting device as USB HDD, save the changes made and then restart your system.
Now you need to change the boot priority in the BIOS. You need to set the 1st booting device as USB HDD, save the changes made and then restart your system.
Note: If your system is not booting from usb stick then following may be
the possible reasons
- Check whether you have selected proper booting media in BIOS settings. It is recommended to select USB-HDD as 1st booting device.
- The usb stick is not made bootable correctly even if the Image file of OS (or any other tool) is written in its memory.
Friday, 24 July 2015
How to Remove Shortcut Virus on Windows
07:09 BackBenchers World
When your folders go missing on your computer or your storage device, or simply created shortcuts in each of them, then they are infected with a virus, actually not a virus. So let's get to know how to get rid of it..
Step 1:
Step 1:
Open the Command Prompt. You can find it under "Accessories" or just search for "CMD" on search bar of your Windows computer.
Step 2:
Step 2:
Find out in what drive of your computer the virus/shortcut are located. Go to My Computer (for Windows 7 or below) or This PC; you'll notice the C, D, E, etc drives.
Step 3:
Step 3:
Go to CMD and type in the commands.
For example, the virus is located in "F" drive, then just type <attrib -h -r -s /s /d f:\*.*, the F beside the D is your drive; simply change it to where drive the virus is located.
- -h: to unhide all files on drive W
- -r: create the files in drive W is free of read-only attribute.
- -s: making all files on drive W to be not part of the system again, so easy in the clear
- f: w drive
- *. *: All files ending in
Step 4:
Press Enter. The bigger the files, the longer the processing takes. Wait until you see "C\:Users.." again. It means that drive will unhide all the folders in your drive.
Step 5:
Step 5:
Check your drive again. The folders are now retrieved together with the shortcut viruses. Remove unnecessary files, the shortcut files that are not supposed to be there. You might find autorun.inf or desktop.ini; simply delete them.
Thursday, 23 July 2015
Notepad Tricks III
12:54 BackBenchers World
In this post here below are shown some cool Notepad trick which can be used in your Windows PC.
Notepad Tricks II
12:17 BackBenchers World
In this post here below are shown some cool Notepad trick which can be used in your Windows PC.
Notepad Tricks I
10:48 BackBenchers World
In this post here below are shown some cool Notepad trick which can be used in your Windows PC.
Tuesday, 21 July 2015
SysKey-SAM Lock Tool
09:53 BackBenchers World
I will first show you what you can do with the SysKey utility and then discuss how much extra security SysKey protection really brings.
The
SAM database is part of the Windows Registry and stores information
about user accounts such as user names and password hashes. The
corresponding Registry file is located in c:\windows\system32\config.
Since Windows NT 4 SP3, the SAM file is partly encrypted. The SysKey
utility allows you to move the SAM encryption key off the computer
and/or configure a startup password.
Using the SysKey utility
To
launch the SysKey utility, type “syskey” at the Start Search prompt of
Windows Vista or Windows 7, or use the “run” option of the Windows XP
Start Menu.

To move the SAM encryption key off the computer, you have, click “Store Startup Key on Floppy Disk.” The tool claims that you will need to insert a floppy disk on startup, which is not really true. Modern computers no longer have floppies, and this storage medium isn’t reliable enough anyway. You can also store the SAM encryption key on a USB flash drive.
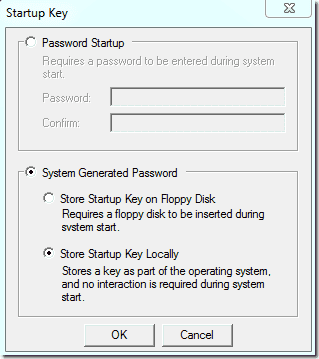
However, the USB stick has to be mounted on drive “A:”. You can assign this drive letter to your thumb drive in Windows Disk Management. If the drive letter A is not available, you have to first disable the floppy disk in the computer BIOS.
The SysKey utility will then allow you
to store a file with the name StartKey.Key on your USB drive. This file
contains the SAM encryption key. Without it, you won’t be able to log on
in the future. Thus, whenever you boot up your computer, you have to
insert this USB stick. Windows will always automatically load the
encryption key from drive A:, and if you set a password with the SysKey
utility, you will have to enter this password whenever you boot up the
computer.


What extra security does the SysKey utility bring
First
of all, neither storing the SAM encryption key on an external drive nor
protecting it with a password can prevent tools such Kon-Boot or the Trinity Rescue Kit
from manipulating the SAM database. These tools are still able to set
an empty password on all accounts. However, after such a manipulation,
it is not possible to boot up Windows without the encryption key on the
USB drive or without the startup password.
Hence, this method will
prevent the majority of wannabe hackers from logging on to the computer
with administrator privileges. It won’t, however, stop real hackers. As
long as an attacker has physical access to an unencrypted system drive,
everything is doable. If you secure the SAM
encryption key then an attacker wouldn’t be able to reach the logon
screen without access to the encryption key.
So does it make sense
to protect all your PCs with the SysKey utility? I don’t think so. The
fact that the tool tries to store the encryption key on a floppy disk
shows that this method is a bit outdated. It is too much hassle for your
users to mess with a USB stick or to use an additional password
compared to the extra protection the tool offers.
However, I
think, the SysKey utility is still useful in some environments. For
instance, you can use the tool to protect laptops or servers where you
don’t want to disable booting from external drives or where many people
would have the time to open the PC and access the system drive. It might
also make sense to protect your own PC this way. Wouldn’t it be
embarrassing if your colleague’s eight-year-old daughter hacks your PC
while you take a coffee break?
The
point is that 99% of all kids out there who call themselves hackers
know about Kon-Boot and the myriad of similar tools, but they don’t know
how to handle SysKey. SysKey was originally introduced to prevent
hackers from cracking passwords in the SAM database with brute force
attacks. And popular hacking tools such SAMInside still can’t handle a protected SAM encryption key.
Speed-up Windows OS
09:10 BackBenchers World
It happens with most of us that our systems becomes slow and show lagging
while opening applications and running various processes. So here is
discussed some important things in detail which help your PC give optimal performance.
1. Remove unnecessary startup objects.
2. Defragment hard disk.
3. Scan hard disk for errors.
4. Disk clean-up & Remove temporary files.
5. Scan for viruses regularly.
6. Check spyware & adware.
7. Uninstall unnecessary programs.
8. Check for registry errors.
9. Remove unnecessary running processes and services from running.
10. Adjust Virtual Effects.
11. Enable Hibernate.
12. Increase Virtual Memory.
2. Defragment hard disk.
3. Scan hard disk for errors.
4. Disk clean-up & Remove temporary files.
5. Scan for viruses regularly.
6. Check spyware & adware.
7. Uninstall unnecessary programs.
8. Check for registry errors.
9. Remove unnecessary running processes and services from running.
10. Adjust Virtual Effects.
11. Enable Hibernate.
12. Increase Virtual Memory.
Remove unnecessary start up objects:
- Open run dialog box with windows key + r and type msconfig and press enter. Goto Startup tab. Here you will find a list of startup objects. Keep only necessary objects and disable rest of them.
- Else press ctrl + shift + esc. It will open task manager and here also you can goto startup tab.
Defragment hard disk:
- Our hard disk data wont saved sequentially. So we need to defragment it to decrease the seek time of your hard disk.
- Goto: My Computer-> Select drive-> Right click-> Properties-> Tools
- Chose Defragment or Optimise (You will see any one of the two)
- Select drive and chose Defragment or Optmise
Scanning hard disk for errors:
- This action recovers bad sectors and fixes file system errors.
- Goto: My Computer-> Select drive-> Right click-> properties-> Tools-> Check.
Disk Cleanup & Remove temp files:
- We perform this step for removing temporary files.
- Goto RUN type %temp% and press enter then delete all files,
- Goto RUN and type Prefetch and press enter then delete all files.
- Instead of the above steps you can also use Disk Cleanup and for that Goto: My Computer-> Select drive-> Right click-> Properties-> General-> Disk Cleanup
Scan for viruses regularly:
- Update your antivirus and scan for Viruses and Trojans regularly.
Check spyware &Adware:
- Download antispyware and adware tools and check your system. Using these softwares could slow down your internet speed.
Uninstall unnecessary programs:
- It’s better to uninstall softwares which you don’t use any more.
Check for registry errors:
- Download Registry error checking tools like tune-up utilities and scan for registry errors.
Remove unnecessary running processes and services from running:
- Use Process Explorer or task manager and remove processes which are not using.
Adjust Visual Effects:
- Right click on My Computer-> Properties-> Advances System Settings-> Advanced-> Setting tab under Performance-> Select Best Performance or Best Appearance as per your requirement.
Enable Hibernate:
- Use Hibernate instead of Shutdown. It is 10 times faster in switching on your system with previous state before you used your PC.
- Goto: Control panel-> Power options-> chose what do power buttons do-> Select Hibernate.
Increase Virtual Memory:
- Virtual memory works like extended RAM. So it helps to increase speed of your applications.
- For this: Right click on My computer-> properties-> Advanced System Settings-> Advanced-> Setting tab under performance-> Advanced-> Change.
- It’s better to set 2-3 times of your RAM size.
Sunday, 19 July 2015
Steganography
11:41 BackBenchers World
 This technique is called as Stenography. It involves hiding data behind images so that only the intended recipients can read the message being sent. I will show you how to hide files inside a picture file. They are almost undetectable, and can be made very hard to get. You can not only hide files in pictures, but music files, videos, and just about anything else.
This technique is called as Stenography. It involves hiding data behind images so that only the intended recipients can read the message being sent. I will show you how to hide files inside a picture file. They are almost undetectable, and can be made very hard to get. You can not only hide files in pictures, but music files, videos, and just about anything else.There are so many S-tools available to hide data behind images. But here you don't need any tool for this. You will need these things:
1) A picture to hide stuff in
2) Files to be hidden
3) A file compression software (I’m using Winrar)
4) Command Prompt
So here we go.
Step 1: Add the data files to a single .rar file and place a image file in the directory containing the rar file.
Step 2: Open Black Box (Command Prompt). [Press windows key + r. Type cmd and press enter. It will open black box.]
Step 3: Select the Disk Drive by writing drive_name: and peress enter. E.g. desktop: or c: or d:.
Step 2: Open Black Box (Command Prompt). [Press windows key + r. Type cmd and press enter. It will open black box.]
Step 3: Select the Disk Drive by writing drive_name: and peress enter. E.g. desktop: or c: or d:.
Step 4: Now type the command copy /b <Image.jpeg> + <File.rar> <New_name.jpeg>. And press enter and its done.
Note: Don't include < > while running the command. These sign(s) are only enclosing a file_name with it's extension.
Note: Don't include < > while running the command. These sign(s) are only enclosing a file_name with it's extension.
Now you would like to know how to excess that hidden file.
What you have to do is only to open that image file with winrar. It will open the rar file hidden behind image file.
What you have to do is only to open that image file with winrar. It will open the rar file hidden behind image file.
For that:
1. Right click on image file containing the hidden rar file.
2. Goto Open with and chose Winrar. And the hidden rar file is opened.
Note: Don't make winrar a default program to open that file. Else it will open the hidden rar file whenever you open it by double clicking on it.
Keylogger
09:35 BackBenchers World
Keylogger is hacker’s and script kiddies’ favorite tool. Keylogger can be a hardware or a software (computer program). It is capable of recording each and every keystroke you enter including mouse clicks and even captures screenshots.
It hardly takes a minute to install this software/hardware in victim’s
system and from next second onwards attacker will get each and every
activity going on victim’s computer. What they are chatting, which site
they are browsing, victim’s username, passwords what’s not? Each and
every activity happening in victim’s system with screenshots will be
recorded. This activity will be saved on victim’s system or it can be
mailed to attacker’s email.
Hardware keylogger: This is a thumb size device. It records all the
keystrokes you enter from the keyboard then saves it in its memory.
Later this data will be analysed. The drawback of this device is that it
can’t record mouse clicks, can’t take screenshots and even can’t mail
and it requires physical access to the machine. Logs are stored in system's local memory.
Software keylogger: This can be installed in victim’s system even if
they use updated antiviruses. There are a lot of softwares available in
market which make a keylogger undetectable by latest antiviruses.
How to fool a keylogger?
Yes we can fool a keylogger. Keylogger’s job is to record all the key strokes we enter. So to fool a keylogger, enter unnecessary keys along with passwords. Confused?
Say your password is 1234. Now how will you enter it. Enter 1 then any unnecessary character say jksfh then 2 then again "£%mygb then 3 then &^%% then 4 then £fsg$^ then 5. Now remove unnecessary characters.
If it is a Hardware Keylogger use Onscreen Keyboard. To open this go to run and type “osk”.
There is also a software tool called "KeyScrambler" which encrypts the plain keystrokes into some hash code. The keylogger will still record the keystrokes but actually it is recording the hash code but not the actual words. E.g.: keyscranmeber : --> password-->@#!@$-> keylogger.
Yes we can fool a keylogger. Keylogger’s job is to record all the key strokes we enter. So to fool a keylogger, enter unnecessary keys along with passwords. Confused?
Say your password is 1234. Now how will you enter it. Enter 1 then any unnecessary character say jksfh then 2 then again "£%mygb then 3 then &^%% then 4 then £fsg$^ then 5. Now remove unnecessary characters.
If it is a Hardware Keylogger use Onscreen Keyboard. To open this go to run and type “osk”.
There is also a software tool called "KeyScrambler" which encrypts the plain keystrokes into some hash code. The keylogger will still record the keystrokes but actually it is recording the hash code but not the actual words. E.g.: keyscranmeber : --> password-->@#!@$-> keylogger.
Wednesday, 8 July 2015
How To Make Bootable USB Stick
09:52 BackBenchers World
Guys Here is discussed to make a Bootable USB Pendrive. To boot
from a pendrive is much more convinent than that of CD/DVD as it is a
faster process. It is difficult to take care of CD/DVD because with regular use
scratches are introduced and this reduce reading speed and also take to
long time to boot. You can use a bootable pendrive to change/recover the
operating system.
There are a lot of tools available in the Market but these can be hazardous as they left your USB stick with permanent memory loss i.e. you
might not be able to use your pendrive for data storage further.
Here is demonstrated Power ISO. Don't worry this is a trusted
computer program and won’t cause any memory loss to your pendrive. You can
download it from Power ISO official site or you may simply click the links
given below.
Here step-by-step procedure is explained with screenshoots. Even if you
find any difficulty then feel free to contact us or you can just drop a
comment.
So here we go.
Step 1. Plug-in your Pendrive.
Step 2. Open PowerISO in administrator mode. For this right-click on
PowerISO icon and select Run as adminstrator.
Step 3. Goto Tools option in
the menu bar and select Create Bootable USB Drive.
Step 4. A dialog box will be as in image below.
Step 5. Here select Image Source File, Destination Derive and Write Method. Finally click
Start.
Note: If your system is not booting from usb stick then following may be
the possible reasons
- Check whether you have selected proper booting media in BIOS settings. It is recommended to select USB-HDD as 1st booting device.
- The usb stick is not made bootable correctly even if the Image file of OS (or any other tool) is written in its memory.
Tuesday, 7 July 2015
Bluetooth Hacking
10:07 BackBenchers World
One of the most popular ways to transfer data between two mobile devices, in range, is via Bluetooth. But Bluetooth just like any other wireless network is prone to attackers. Bluetooth Hacking could be classified into following three categories:
1. Classifications of Bluetooth Hacking
Bluejacking, though classified in Bluetooth hacking, isn't exactly harmful to the user in any way. It involves sending of unsolicited messages by an attacker to other Bluetooth enabled devices. The messages are sent in such a way, that the other user HAS to see the message. This is usually done by creating a new contact with the contact namefield as message, which the attacker want to send to the victim. This does not cause any changes to the victim's phone, except getting him confused about what has happened.
This method, as already said, not being harmful, may for some period of time confuse the user which may lead to think that their phone has been hacked.
Bluesnarfing is an advanced Bluetooth hacking technique, which is done with the help of advanced equipment, and at the same time, being in a certain range of target. A successful exploitation lead the attacker to gain full control of the hacked device, with the ability to make phone calls, eavesdrop phone conversations, read and write messages, and even perform network activities. The attacker uses OBEX push profile to attempt to send an OBEX GET command to retrieve known filenames such as telecom/pb.vcf. The enhancement to this Bluesnarf++ connects to the OBEX FTP server to transfer the files.
Bluebugging is similar to Bluesnarfing, but the attacker gets full control of the device in Bluebugging. This is similar to Trojans used in computers. The attacker also gets to execute remote commands on the victim's device.
2. Tools used for Bluetooth Hacking
Bluescanner: The first thing one would need to know in Bluetooth hacking, is to identify the devices having their Bluetooth turned on. Bluescanner is a tool for windows XP SP2, which helps in discovering the Bluetooth devices as well as tries to get all the information possible about each and every devices found. You can get this tool here.
Bloover: Bloover is a mobile application that runs on J2ME based handsets. It is an audit tool, which could be used by mobile users, in order to find out, if their phone or the phones in the nearby are vulnerable to Bluetooth attackers.
Since, it is just on audit tool, after finding out the vulnerability, it doesn't allows the attacker to send sms using the compromised phone.
BT Browser: It is a J2ME mobile application, which offers the same functionality similar to that of Bluescanner. This application works on phone, which supports JSR-82 such as Nokia 6600 and Sony Ericsson P900.
BTAudit: It has a set of two tools dedicated to Bluetooth hacking. The division is done on the basis of protocol scanned. The two protocols are L2CAP PSMs (Protocol Service Multiplexer) and the RFCOMM Channels. You can get it here.
BTCrack: BTCrack is a software to break bluetooth pass phrase by bruteforcing. It captures the pairing exchanges and then bruteforces the passkey and the link key.
BTCrawler: It is a Bluetooth device scanner for windows Based mobiles. It could also perform other bluetooth hacking techniques, namely BuleSnarfing and Bluejacking, to the vulnerable devices in range.
Turn Your WiFi Into HiFi
09:12 BackBenchers World
Have the slow Wi-Fi speed troubled
you? You want high speed, but you are not getting any solution for this? Now
it's time to get rid of this problem. Here are discussed some tips for the same.
Setup the router in centre
For fast speed it's very necessary to setup router at proper
place. You should install router at centre or nearby to centre of your home so
that signal could reach at each any every corner properly. If there are various
floors in your home or office, then it would be better to install router at top
floor. Electronic devices produce interference in Wi-Fi signal, so always keep
in mind that devices like microwave, TV, refrigerator, cordless phones, halogen
lamps etc. are to be kept at least 10 feet away from router.
Boost your Wi-Fi with booster antenna
Generally router has one or two
antenna(s), but due to this signal doesn't reach to each any every corner. So,
in this situation, it would be apt to install booster antenna for strengthening
the signal. It will widen Wi-Fi range and increase speed also.
Not to share Wi-Fi network name (SSID)
Do not share your Wi-Fi Network Name
with any of neighbrour or anybody else. For hiding Wi-Fi network name, turn off
Service Set Identifier under Broadcasting Option. It would be better if you add
password to your Wi-Fi Network Name.
Remove
Interference of one Wi-Fi signal with
another Wi-Fi signal causes weakening of signal. To get rid of this problem,
Wi-Fi Stumbler or Wi-Fi Analyzer could be used. This will prevent interference
of other's Wi-Fi signal with your Wi-Fi signal and in turns it will result in
increased Wi-Fi speed along with strengthening the signal.
Latest technology always rocks
The best option for high speed Wi-Fi
is to use latest technology. Means always use up-to-date hardware. Wireless
'a', 'b' and 'g' has become old and it works slowly. Wireless 'n' is the latest
version and it gives very fast speed. Using wireless n card with your laptop or
PC along with wireless n router will give you best possible results in terms of
speed.
Windows 10 Technical Preview
08:46 BackBenchers World
It was hoped from last few days, Microsoft would launch Windows 9 as its new Operating System. But recently the company has launched Windows 10 Preview instead of Windows 9. Microsoft launched Windows 8 operating system about 2 years back, but it could not get much success. Now Windows 10 is designed in such a way that it can run on mobile phones, tablets, and personal computers easily. Yet the company has launched Preview of new OS, it is expected that it will be available in market by July 2015. The new OS is built with various features which users were missing in Windows 8. From phones to the gaming console, it can run on different devices.
START MENU RETURNS: In the new OS you will be getting Start Menu again. Actually, Microsoft removed Start Menu in Windows 8, but users didn't like this change. This time Microsoft took a U-turn and added Start Menu in its new OS again. Similar to Windows 7, Start Menu is given on bottom-left corner on the desktop in Windows 10. Users will get Touch experience like Windows 8.1 operating system. Instead, users will also be having an option to give a similar look as that of windows 7 to the new OS. Actually, Windows 10 is a combination of the classic look of Windows 7 and modern user interface. In this new OS, you can also change the layout.
UNIVERSAL APPS: Microsoft's new OS will also support apps. Means users of Windows 10 Operating System can use all the apps of Windows store. These apps will also run on your desktop. You can also re-size these apps as per your choice. Besides this, new OS will also support older apps available on app store. Important functions can be accessed with Context Menu. Generally, the meaning of Windows Universal App is that all your apps can run on Windows 10 devices(desktop, phones, and gaming console).
VIRTUAL DESKTOP: Microsoft has given an option of Virtual Desktop for Enterprises and Power users. You can switch different desktop as per your need with the help of Virtual Desktop. This will appear very similar to Virtual Desktop. Users can have different desktops for different projects and file according to their convenience. This feature is inbuilt in Windows 10. Further, you can have an overview of all running apps with the help of task-view and can move to the virtual desktop and manage them easily. This is like adding more screens to your phone or tablet which can be viewed by swiping.
TASK VIEW: To improve multitasking in this new OS, Task-View Button (alt-tab) is given. Task-View button is integrated on the taskbar and can be used for switching to different apps on Virtual Desktop. Diminished preview of all the open apps can be seen together.
CONTINUUM: This is the most interesting feature of Windows 10. This feature is for 2 in 1 devices. Actually, Continuum feature means that the user interface of new OS will change automatically according to the device. For example, suppose you are using a Hybrid Laptop-Tablet then you will be having a standard desktop, but as soon as you unplug the keyboard, it will switch to Tablet mode. This time it has come up with Touch Button.
NO METRO AAPS: Windows 10 also doesn't have large tiles on Home Screen like other versions of Windows. You can manage your items or can apply a background picture of your choice. You can switch from Tablet mode to Touch Screen mode without keyboard and mouse. The Charms Bars of Windows 8 haven't been removed completely. Instead, these are improved. Windows 8 users, who are already familiar with this feature can further use it.
IMPROVED SNAP: Snap function has been improved in Windows 10. With this feature, windows can be tiled horizontally and vertically. Snap Assist feature works according to you choice. If you want, you can snap windows into new screen or tile.
HIDE METRO INTERFACE: It is not clear yet, has the Metro Interface been completely removed or not. Actually this is a better option for Hybrid, but while talking about Desktop, Microsoft has given a Check Box at its place in which 'Never Show Me The Metro Interface' option will be there.
EASY SHUTDOWN: Windows 8 users were waiting for an easy Shutdown feature. To Shutdown PC in Windows 8 users had to go to Charms firstly then Log off and then finally Shutdown. Now Windows 10 has given a much better Shutdown function. You will be able to see Shutdown option just by pressing alt+f4.
UNIVERSAL SEARCH: Universal Search function is given in Windows 10. This option works for both searching PC and Web. Now you don't have to go to browser for searching the net. If you have searched something in Search option of Start Menu, it will not only show the search results of the apps and files existing on your computer but also give search results from the internet. Microsoft's Universal Search is somewhat similar to Apple OS X.
You can Download ISO file for 32-bit and 64-bit version below:
Monday, 6 July 2015
Unblock Blocked Sites Cum Become Anonymous On Internet
10:32 BackBenchers World
This question revolves around a single term called "IP ADDRESS". Hackers know that they are doing a crime and will be traced if they perform an attack directly with their original IP address. So they hide their original IP address. It becomes difficult for the investigators to trace them if an attacker hides his original IP address.
Hiding The Identity
This is possible with some wonderful tools called Proxies and VPNs. There are a number of services available to hide our identity online. It can be a free service or paid service. In paid services, since we pay some money, it will be more reliable.
1. Basic concepts about Proxies
Proxy Servers: A Proxy acts as an intermediary between our computer and the target server. It means we are not directly interacting with the servers. Instead, we will interact with the proxy server which in turn interacts with the target server. All the requests sent from our computer will go to the server via proxy server. Similarly, all the responses from the server will come back to our computer via proxy server.
2. Types of Proxy Server
Web Based Proxy: When we use websites which give a facility to user to change the online identity through their web proxy servers then we say its known as WBPS. For Example: www.ninjaproxy.com www.kproxy.com www.anonymzier.ru
Application Based Proxy Servers: These are the proxy servers in which we try to use application software of the proxy servers which directly connect us to the pool table of proxy servers and gives us a fake IP address to surf internet hence the banning policy will not work much as we are not traveling the content directly through the HTTP and port number 80. For Example, UltraSurf, HotSpot Security Shield.
VPNs: Virtual Private Network: A VPN is a private network that connects remote networks through a public network such as the internet. VPNs are also very similar to proxies. VPN provides security by using some tunneling protocols and encryption mechanisms. For Example, OpenVPN, Proxpn, Cyberghost, Hotspotshield, Logmein Hamachi
Plug-In Based Proxy Server: AnonymoX.
3. What makes the difference?
If you will browse the target website without any proxy, then your original IP will be visible to that website. If you browse the internet with proxy then your original IP will be hidden and proxy's IP will be visible to target website.
4. TOR- The Onion Routing
TOR is one more beautiful tool to hide your identity. As the name represents, it contains too many router layers (nodes) like an onion. Using TOR is one of the best way to hide your identity online since it uses a chain of nodes where each node doesn't know any information about the traffic path except the details of next receiver node and previous sender node from which it is receiving the data.
How to use TOR
First download the TOR bundle here. It contains a client application you need to run. It gets the information about the node available when executed(run). Then it selects a random path through which the traffic will be passed towards the destination.
Note: The TOR browser is specially intercepted by Indian Govt. in India.
Subscribe to:
Comments (Atom)
































