The SysKey utility, also called the SAM lock tool, is a built-in
Windows tool that allows you to secure the Security Accounts Management
(SAM) Database. It can be helpful for preventing hackers from cracking
Windows passwords.
I
will first show you what you can do with the SysKey utility and then
discuss how much extra security SysKey protection really brings.
The
SAM database is part of the Windows Registry and stores information
about user accounts such as user names and password hashes. The
corresponding Registry file is located in c:\windows\system32\config.
Since Windows NT 4 SP3, the SAM file is partly encrypted. The SysKey
utility allows you to move the SAM encryption key off the computer
and/or configure a startup password.
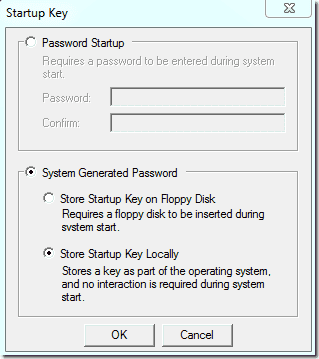
Using the SysKey utility
To
launch the SysKey utility, type “syskey” at the Start Search prompt of
Windows Vista or Windows 7, or use the “run” option of the Windows XP
Start Menu.
To
move the SAM encryption key off the computer, you have, click “Store
Startup Key on Floppy Disk.” The tool claims that you will need to
insert a floppy disk on startup, which is not really true. Modern
computers no longer have floppies, and this storage medium isn’t
reliable enough anyway. You can also store the SAM encryption key on a
USB flash drive.
However,
the USB stick has to be mounted on drive “A:”. You can assign this
drive letter to your thumb drive in Windows Disk Management. If the
drive letter A is not available, you have to first disable the floppy
disk in the computer BIOS.
The SysKey utility will then allow you
to store a file with the name StartKey.Key on your USB drive. This file
contains the SAM encryption key. Without it, you won’t be able to log on
in the future. Thus, whenever you boot up your computer, you have to
insert this USB stick. Windows will always automatically load the
encryption key from drive A:, and if you set a password with the SysKey
utility, you will have to enter this password whenever you boot up the
computer.
What extra security does the SysKey utility bring
First
of all, neither storing the SAM encryption key on an external drive nor
protecting it with a password can prevent tools such Kon-Boot or the Trinity Rescue Kit
from manipulating the SAM database. These tools are still able to set
an empty password on all accounts. However, after such a manipulation,
it is not possible to boot up Windows without the encryption key on the
USB drive or without the startup password.
Hence, this method will
prevent the majority of wannabe hackers from logging on to the computer
with administrator privileges. It won’t, however, stop real hackers. As
long as an attacker has physical access to an unencrypted system drive,
everything is doable. If you secure the SAM
encryption key then an attacker wouldn’t be able to reach the logon
screen without access to the encryption key.
So does it make sense
to protect all your PCs with the SysKey utility? I don’t think so. The
fact that the tool tries to store the encryption key on a floppy disk
shows that this method is a bit outdated. It is too much hassle for your
users to mess with a USB stick or to use an additional password
compared to the extra protection the tool offers.
However, I
think, the SysKey utility is still useful in some environments. For
instance, you can use the tool to protect laptops or servers where you
don’t want to disable booting from external drives or where many people
would have the time to open the PC and access the system drive. It might
also make sense to protect your own PC this way. Wouldn’t it be
embarrassing if your colleague’s eight-year-old daughter hacks your PC
while you take a coffee break?
The
point is that 99% of all kids out there who call themselves hackers
know about Kon-Boot and the myriad of similar tools, but they don’t know
how to handle SysKey. SysKey was originally introduced to prevent
hackers from cracking passwords in the SAM database with brute force
attacks. And popular hacking tools such SAMInside still can’t handle a protected SAM encryption key.